Modules
Discovery
This is the section where the subnet information used in the data center is identified. This information allows for identifying the entire inventory of the server. The subnets are scanned by the discovery service. To add a subnet, enter the IP address and CIDR (classless inter domain routing) information in the portal interface. Once this information is entered, the scan is automatically performed by the Helios-Platform Discovery Service
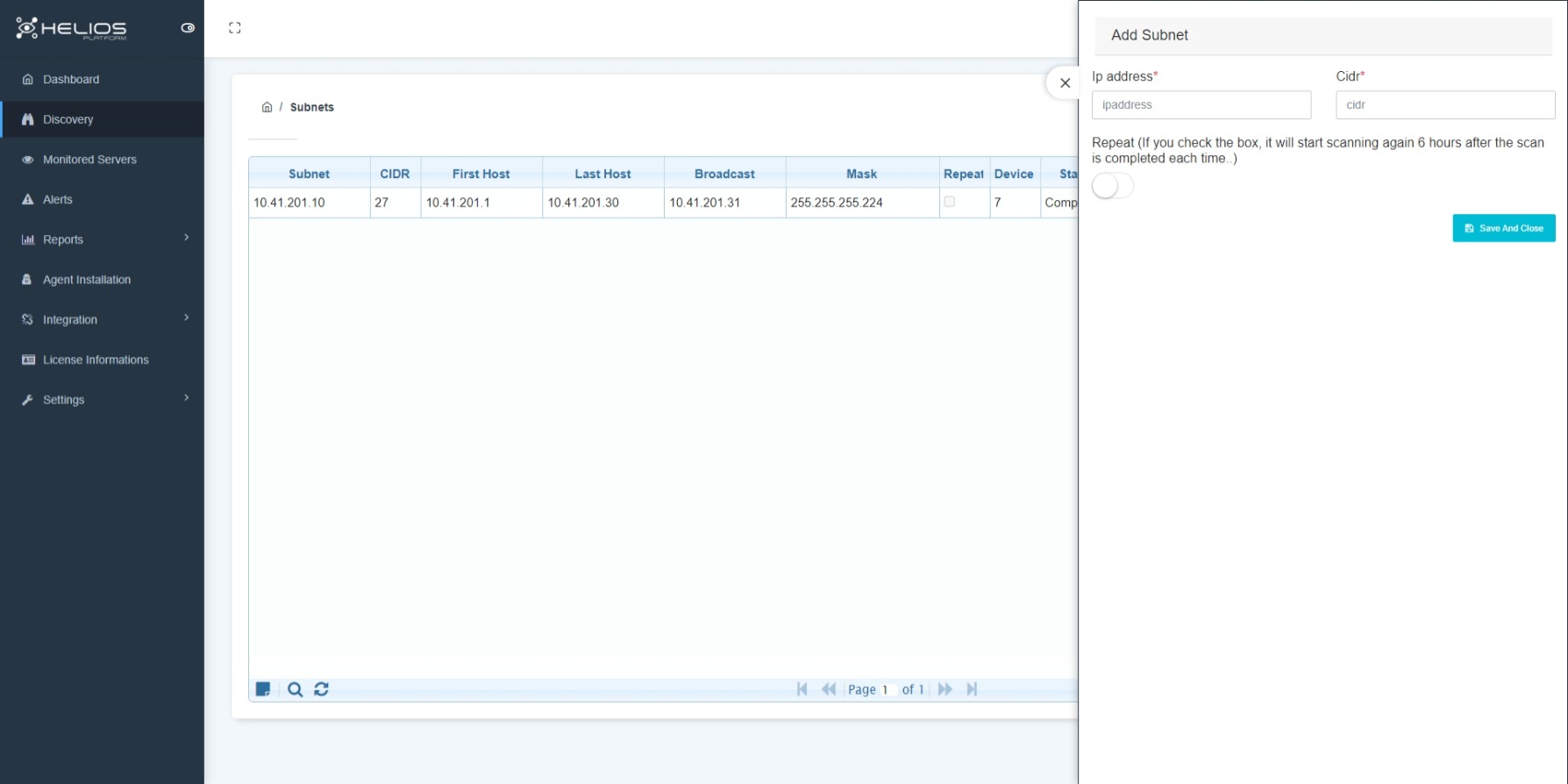
Features
- Detecting the device connected to the server operating system by scanning the IP address of the subnets.
- Detecting the devices without an installed agent.
- Inventory detection independent of the platform (virtual/physical) where it runs.
- Detecting open port information on the server.
Monitoring
The discovered servers are displayed in the Helios-Platform portal. Entering the ownership information of the servers and the information required to categorize the servers (criticality/location, etc.) provides convenience in mapping and reporting.
Warning
Monitoring is conducted by installing the agent.
Click here Agent Installation for more information.
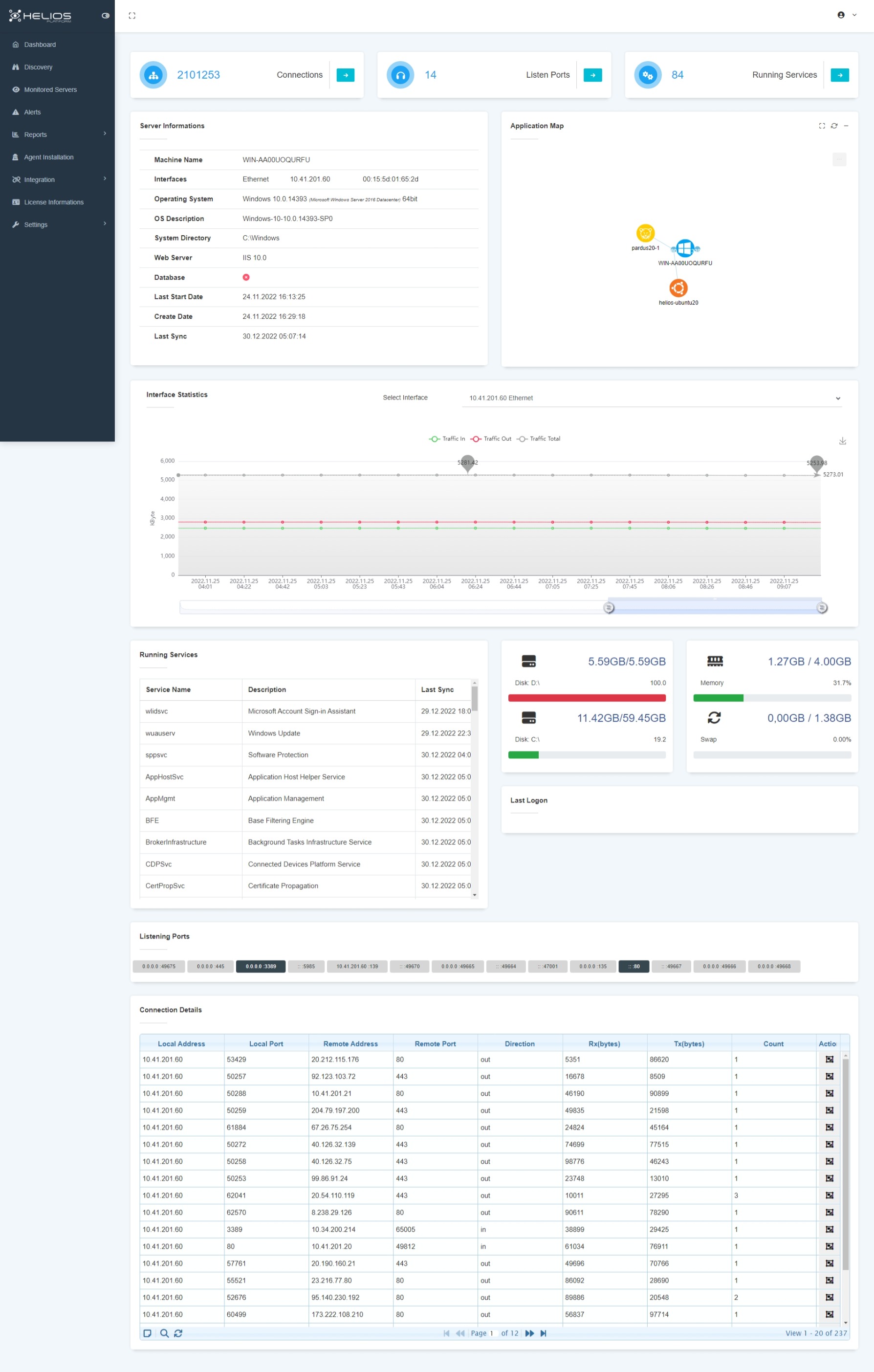
You can easily access information in the server details;
- Displays detailed information on the server, such as web server or database, its version, operating systems, etc.
- Server application map: Schematic representation of open ports on the server, applications installed on those ports, and other servers connected to those applications.
- Displays features of other connected servers and details depending on the direction of connection at IP level.
- Time-filtered graphical representation of information, according to traffic direction (inbound/outbound).
- Time-based display of the service information chart running on the server.
- Hardware information of the server; detection of disk-fullness rate-memory/RAM information.
- Views the last 3 logins to the server.
- Identifies the ports that do not pass traffic by presenting information on the ports that are connected/not connected to the server.
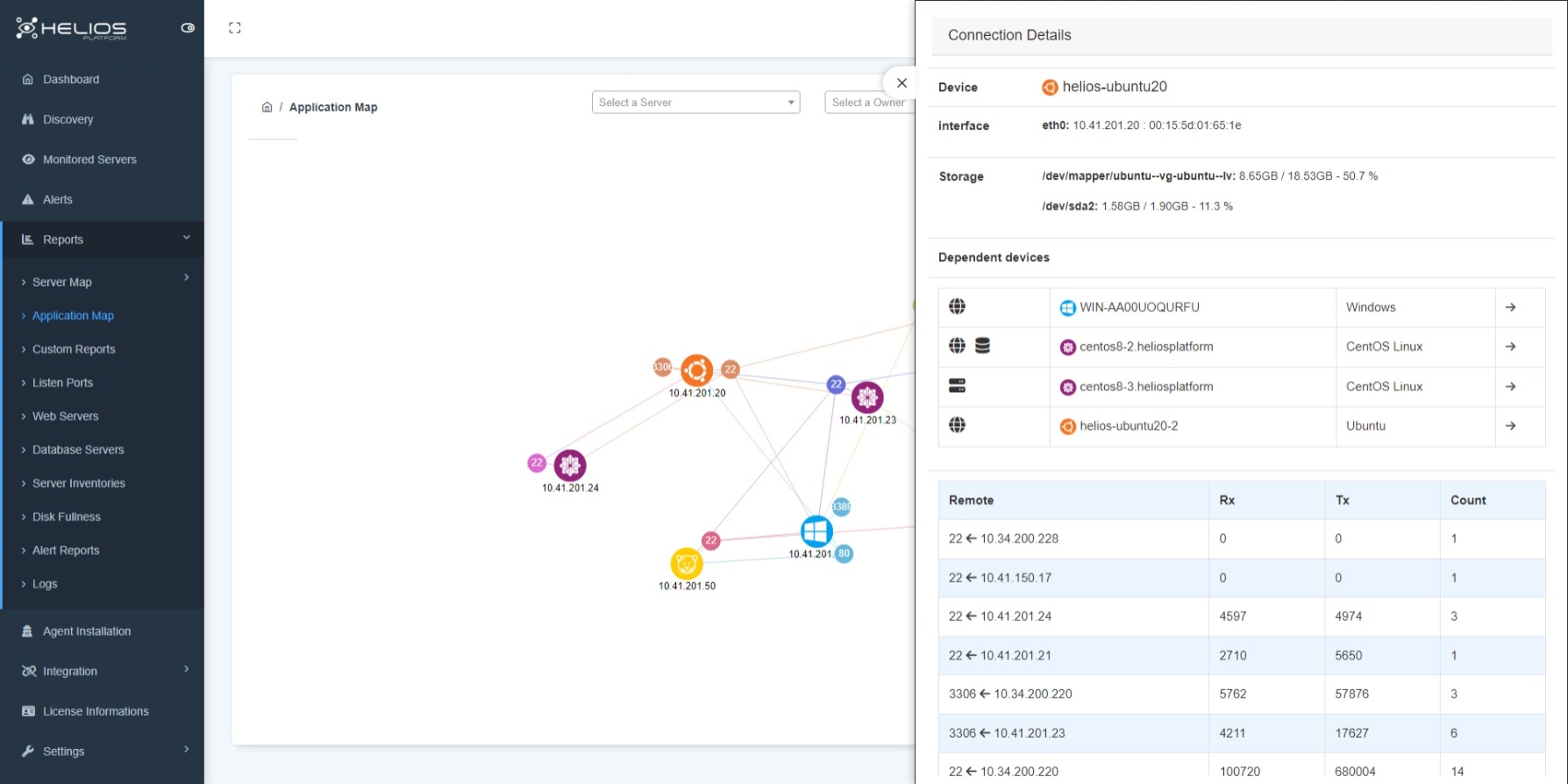
Mapping
On the Helios platform, a visual graph displays the servers discovered, the applications on the servers, and the ports over which these applications communicate with each other. The operating system of the servers is also displayed as passable in the chart.
In the Helios-Platform Application Map, you can select the servers only that you want to view.
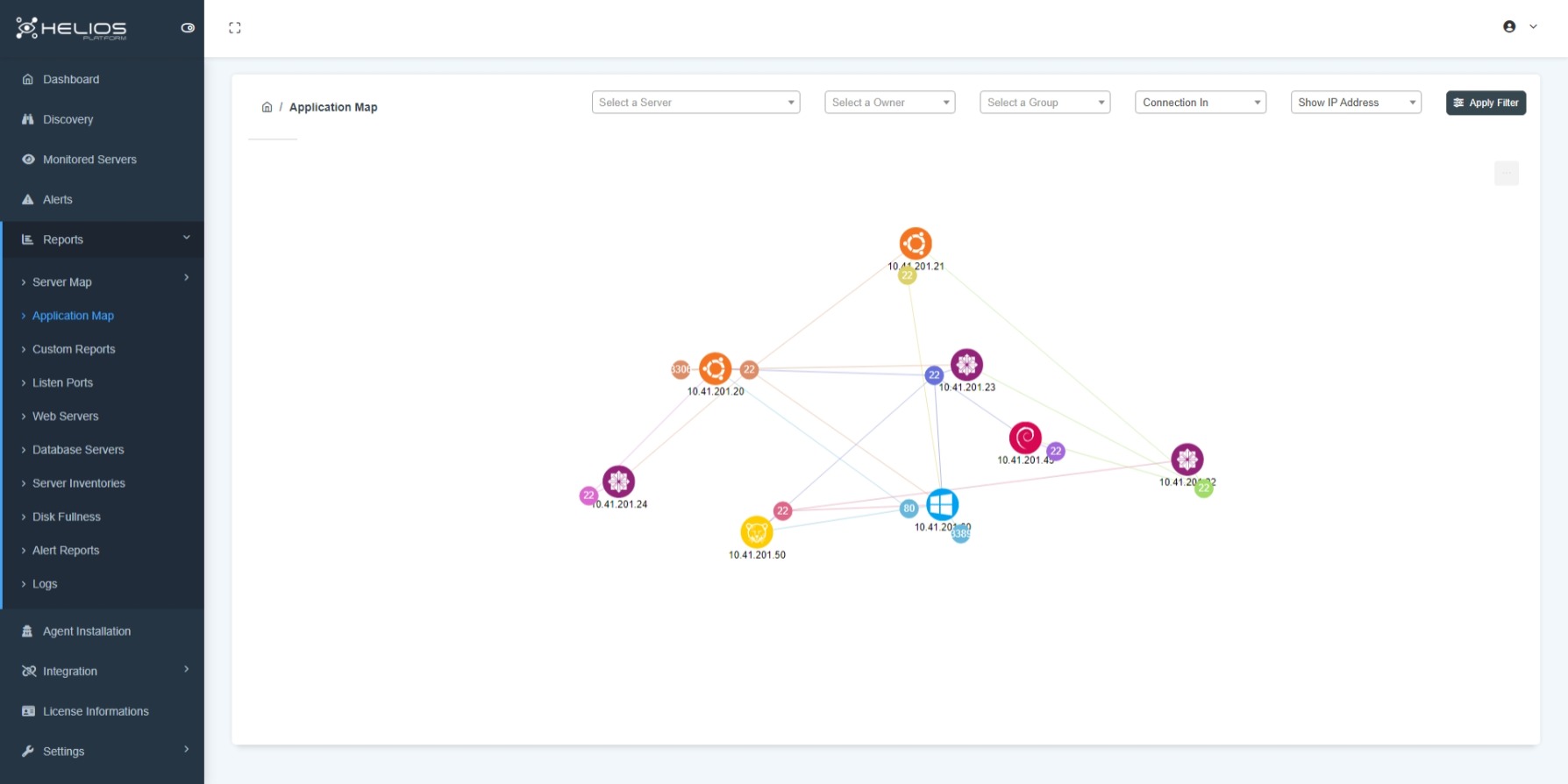
The criteria to be used for that selection can be created with:
- Server Ownership.
- Server group (site-based, criticality status, etc. can be created.)
- Connection direction.
- IP address/Hostname filter.
Alerts
Depending on the criticality of the servers, certain threshold values are selected for the server and an alarm notification mechanism is established. Thus, you will be informed before any problems occur on servers that reach certain threshold values.
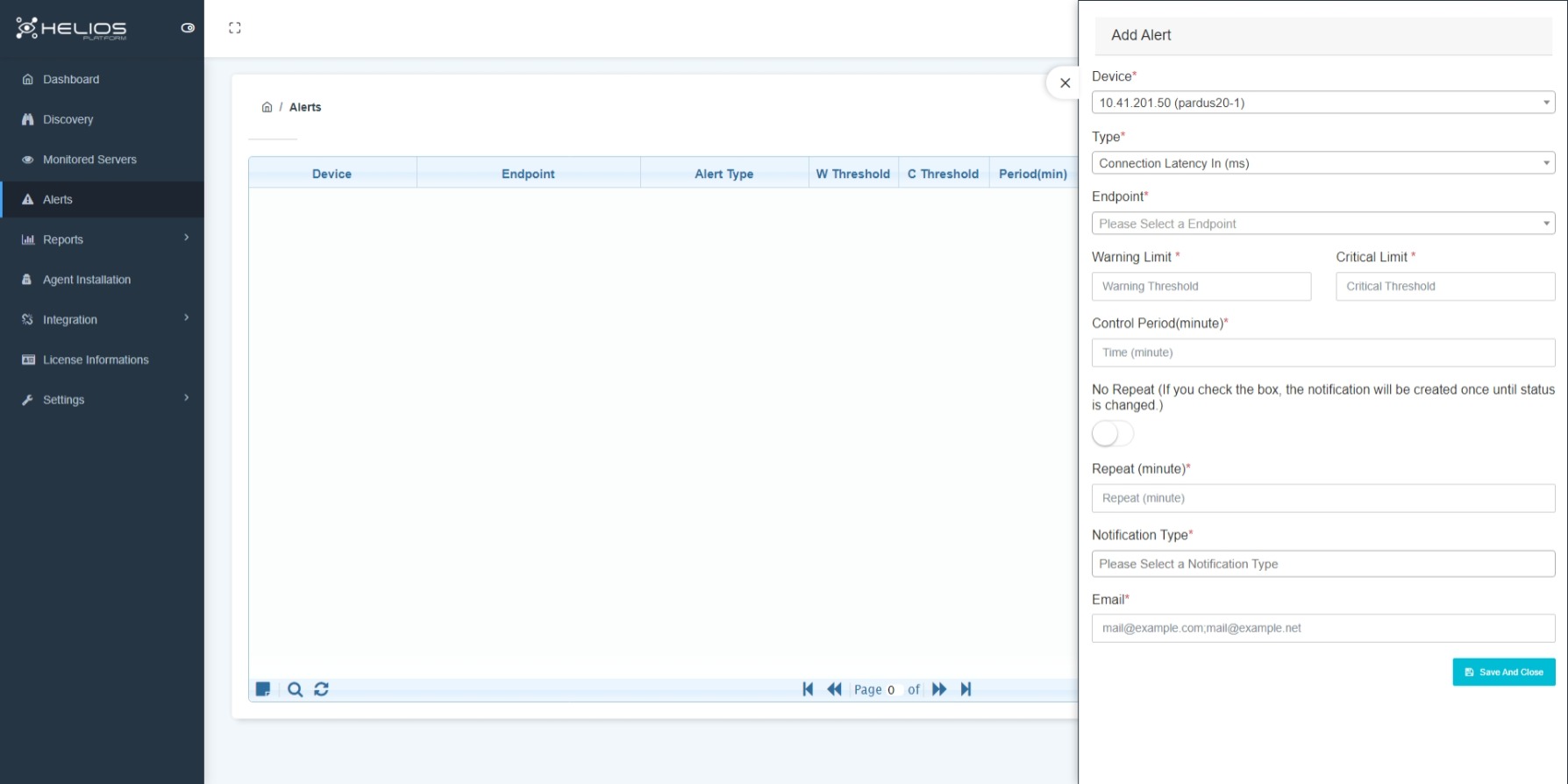
The metrics used to create alarms specific to the server;
- Lag times between servers.
- Total connection times.
- Sizes of data incoming and outgoing to/from the server.
Note
Threshold values are determined using these criteria and a warning is sent to the designated email addresses.
This allows you to take proactive action before any problems occur in your systems.
Reports
In Helios-Platform, various reports specific to the needs can be created for the visible information on the portal.
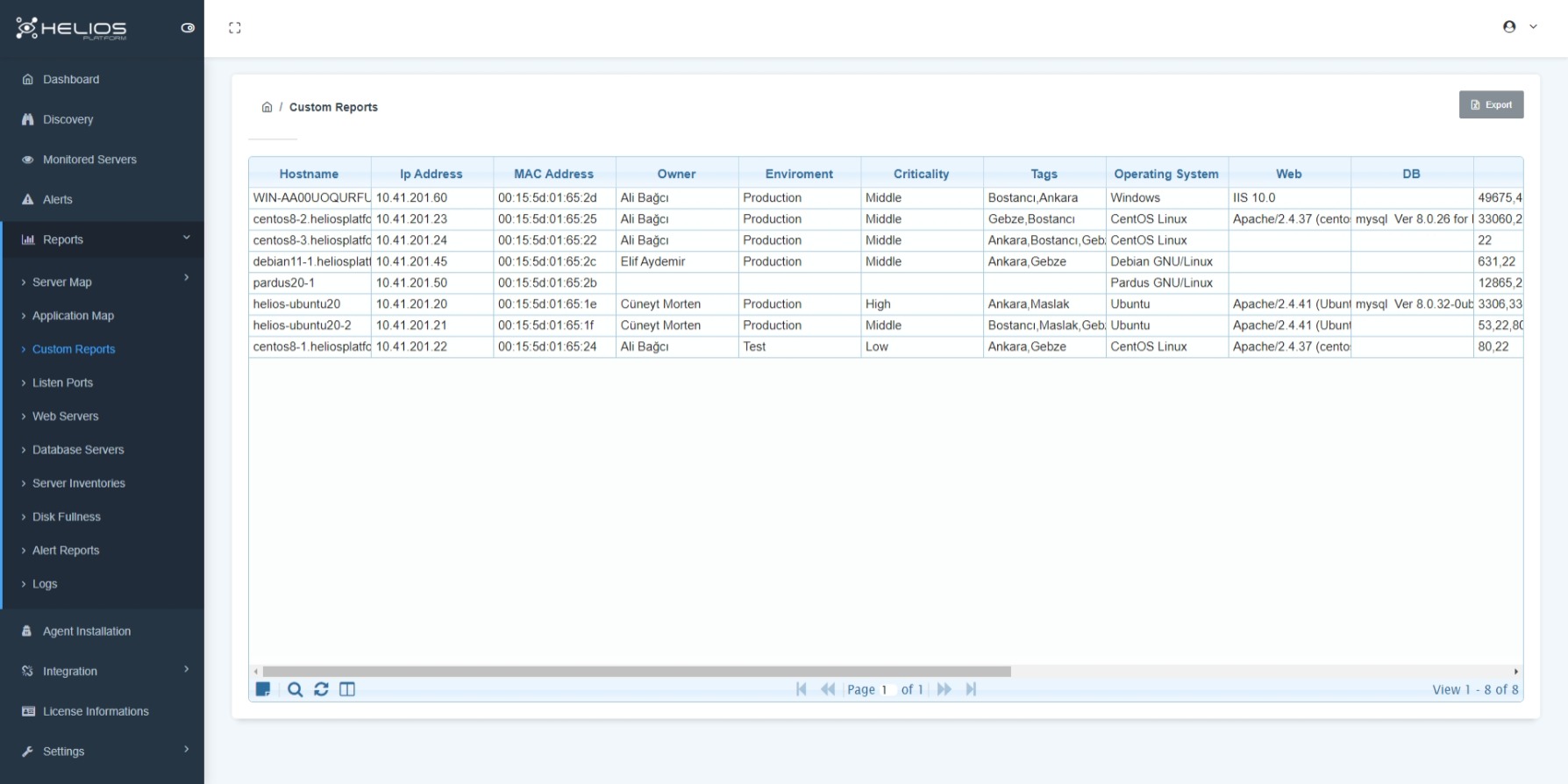
Report types;
- Customizable reports (reports customized according to server ownership, server location, criticality, etc.)
- Server inventory report.
- Open port info report with/without active traffic.
- Web servers/database servers report.
- Disk reports (information about the size of the server used/its space).
- User/alarm/service log reports.
eBPF
eBPF (extended Berkeley Packet Filter); is the technology used for viewing and analysing network traffic and tracking the system performance. With the EBPF integration into Helios-Platform, traffic analyses of the discovered servers are carried out and a proactive approach is adopted to the problems.
Warning
It can be used on eBPF’s Linux Kernel 4.2 or Windows Server 2019 and higher operating systems. It can be used on eBPF Kernel Space for networking, debugging, tracing, firewall and more.
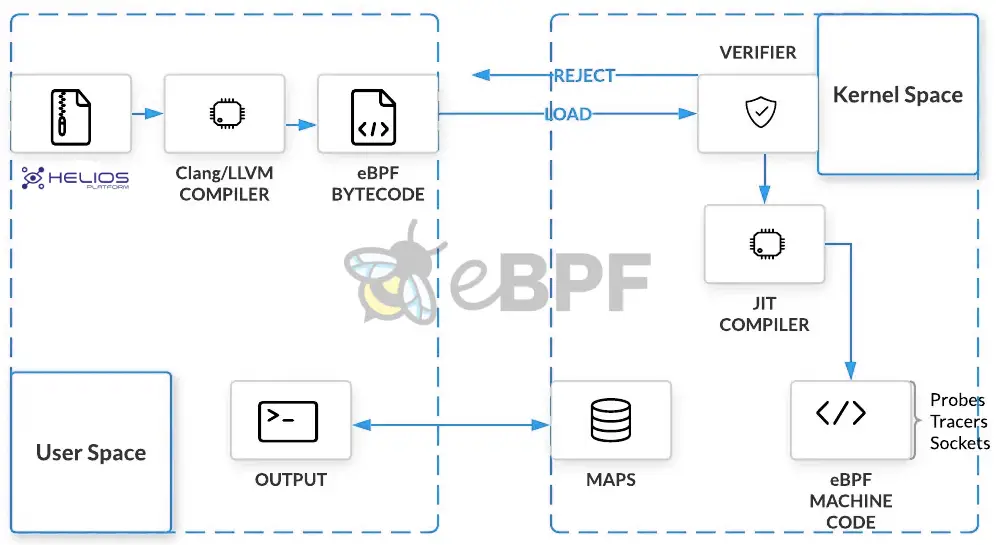
eBPF usage areas;
- Security.
- Network operations.
- Monitoring and profiling.
- Observability.
Microsegmentation (Zero Trust Architecture)
Microsegmentation is a security technique that breaks data centers and cloud environments into segments down to the individual workload level. Organizations implement microsegmentation to reduce attack surface, achieve regulatory compliance, and contain breaches.
Microsegmentation detaches segmentation from the network by leveraging the host workload firewall to enforce policy across east-west communication, not just north-south.
Sometimes microsegmentation is referred to as host-based segmentation or security segmentation. This advanced approach emerged in recent years to deliver more effective segmentation and visibility to ease compliance.
Warning
Microsegmentation uses the host workload instead of subnets or firewalls. Each workload operating system in the data center or cloud contains a native stateful firewall, such as iptables in Linux or Windows Filtering Platform in Windows.
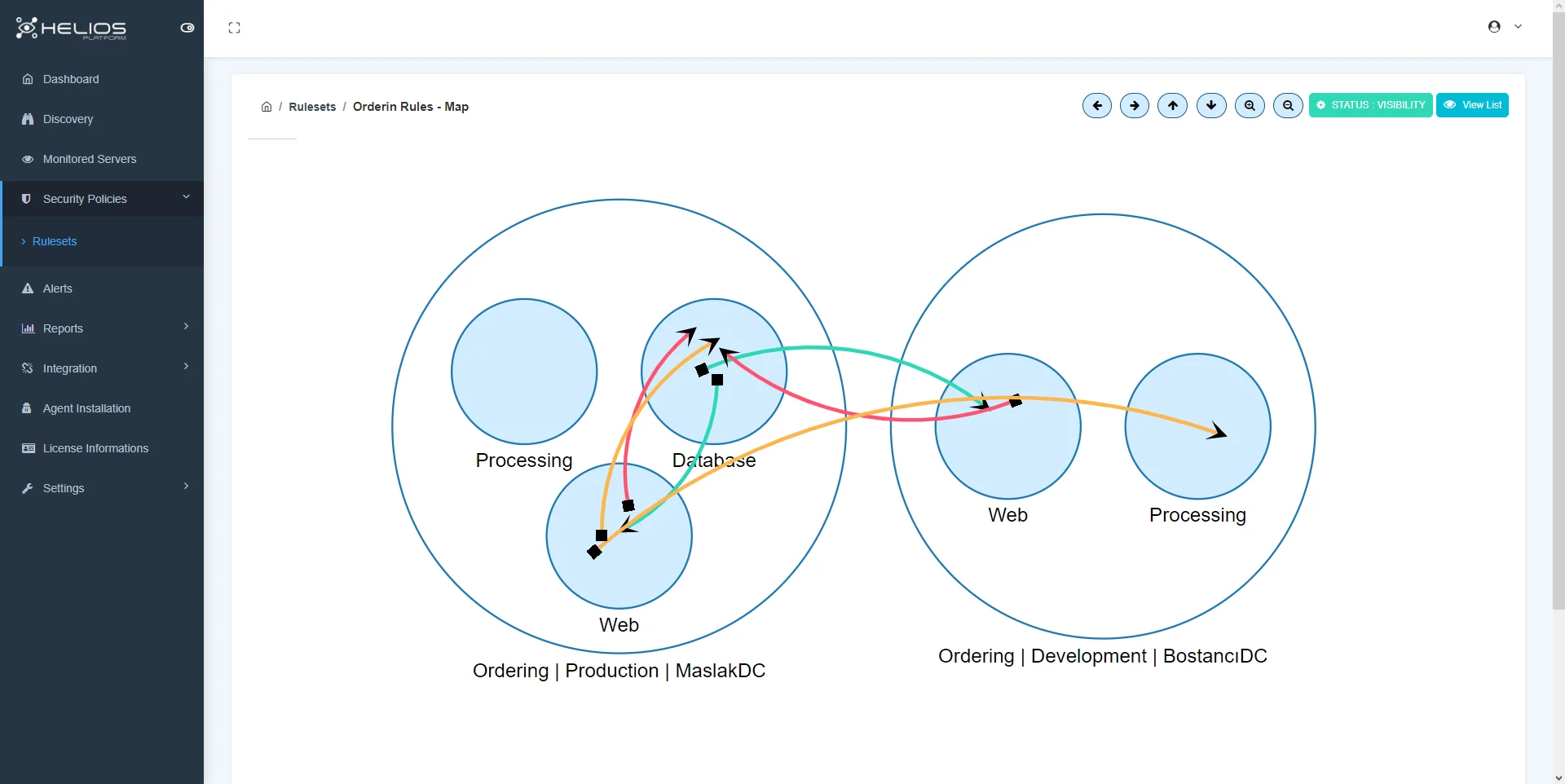
How microsegmentation works;
- Reduce attack surface: Gain complete visibility of the network environment and control lateral communication access to reduce attack vulnerabilities.
- Achieve regulatory compliance: Isolate systems with regulatory mandates to provide granular policy controls for compliance.
- Improve breach containment: Monitor traffic against secure policies and control lateral movement to reduce breach size and response time.
What are the Possible Benefits and the Disciplines Gained?
Many benefits come from the network infrastructure segmented into smaller segments and the permanent monitoring of these infrastructures.
With easier visibility on network movements, the dominance of traffic flows of Applications is increasing, leading to an increase in general awareness on the network.
It forms a basic infrastructure at the point of providing the cyber security discipline required for zero trust architecture. The attack area for malicious behaviors is narrowed and possible threat prevention moves are facilitated.
Where to start?
The primary condition for a successful micro-segmentation project is the complete extraction of the right inventory. Defining the relational networks of applications and processes of the inventoried inventory will be the secondary step. With this relational network, it should be aimed to reveal which applications and processes our inventory has, and how they communicate with different systems and different users.
Note
Click to view more content and user guides on Security Policies.